Configure Entra Domain Services for use with AVD
This section applies when you have one of the following situations:
-
You have a cloud-only environment. That is, you only have Entra ID and you do not have an on-premises Active Directory with Azure AD Connect.
-
You do not want to connect your on-premises domain to the Azure cloud via a VPN.
If any of the above applies, then the Entra Domain Services service provides the Active Directory component required by the Azure Virtual Desktop.
Preliminary Considerations
Important: When you use Entra Domain Services with cloud-only environments, all your AVD users are required to reset their passwords before they can use AVD. This is because the password hashes must be regenerated to be compatible with ADDS (traditional AD). This is one time only after Entra Domain Services has been provisioned. See the Microsoft documentation for details.
-
Entra Domain Services' lowest tier is "standard." This tier's retail cost is a fixed rate of ~$110/month (As of January 2021, prices may vary.) Generally, this tier covers most environments that are under 25,000 AD objects and 3,000 auth/hour. More pricing details can be found here.
-
You do not have Domain Admin rights over the AD. However, you are given all the necessary management rights to join machines to a domain, edit GPOs and OUs, etc.
-
Entra Domain Services is a one-way sync. Changes made directly to the AD are not synchronized back up to your Entra ID. Likewise, changes such as adding users, GPOs, OUs, etc. are persistent. However, if the Entra Domain Services is deleted, the changes are lost.
-
If there are domain-level changes that must be made, such as adding GPOs or OUs, a "Management VM" must be created with RSAT installed to edit the AD. See this Microsoft article for more information.
-
Entra Domain Services cannot be moved to another resource group or subscription. It must be deleted and recreated. Keep this in mind if you are using a temporary RG or subscription for PoC purposes.
-
The domain name cannot be changed. If you are building a PoC and wish to use a temporary domain name, you must delete and recreate the domain.
Entra Domain Services Design Principals
Entra Domain Services is a way to provide domain services such as LDAP, Kerberos/NTLM, domain join, and group policy to various other Azure resources that require them. It takes your cloud-only Entra ID and presents it as if it were a "traditional" or "on-premises" Active Directory to VMs and apps in Azure. It can be thought of as "Active Directory-as-a-service."
This is a sample configuration of Entra Domain Services.
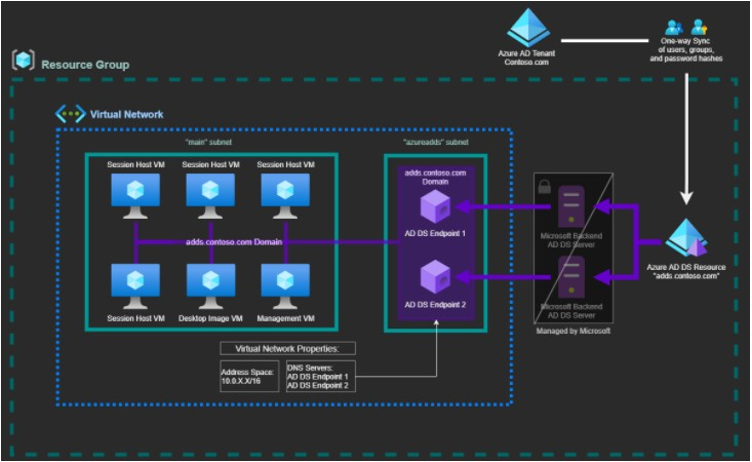
Notes:
-
The subnet that Entra Domain Services uses for its endpoints must be separate from your other subnets. It must contain only Entra Domain Services endpoints. Do not attempt to add VMs to this subnet. In addition, it is recommended that you do not link this subnet to your Nerdio Manager environment in the Settings section.
-
You must set the DNS settings on your virtual network to point to the AD DS endpoints, so that your VMs can resolve the domain.
-
Entra Domain Services is a resource object. It can be placed in a resource group and likewise deleted. It is recommended that you set a "lock" to prevent accidental deletion of this resource.
Create an Entra Domain Services Domain
It is recommended that you follow the Microsoft Guide when creating the environment:
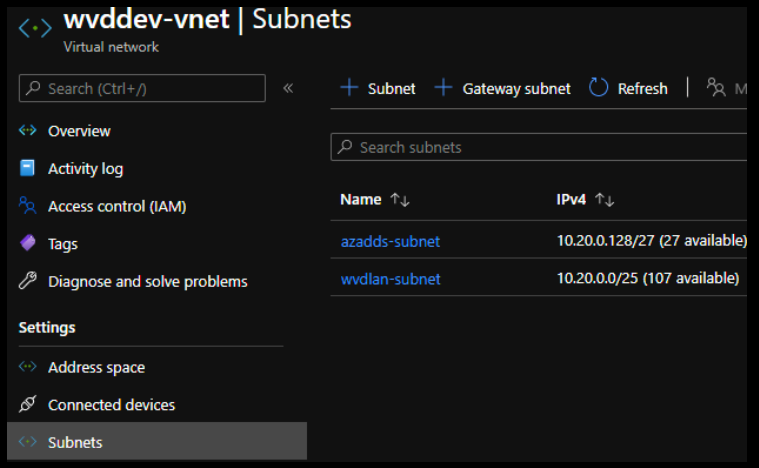
Tip: You need a separate subnet to use for your session hosts. For better organization, before you create your Entra Domain Services, you can make the VNet with two subnets as shown in this example (substitute the IP ranges and names as desired):
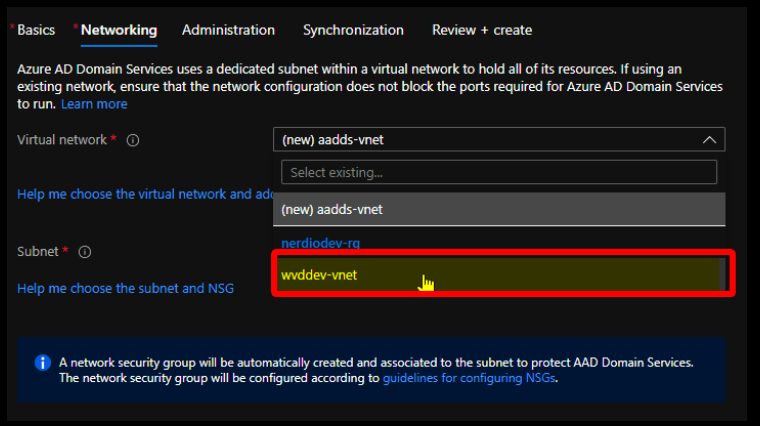
In the Networking tab, specify the VNet and Subnet you previously created.
Configure Nerdio Manager for Entra Domain Services
When Entra Domain Services is up and running, Nerdio Manager must be configured to utilize it.
To configure Nerdio Manager for Entra Domain Services:
-
Navigate to the Settings > Azure environment.
-
Make sure that the Display non-AD synched users option is set to Enabled.
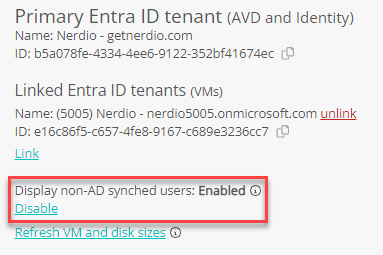
Note: This allows you to assign users that are cloud-only within Nerdio. Without this setting, users do not appear within the system's web portal for assignments or roles.
Tutorial: Enable User Accounts for Entra Domain Services
Tutorial: Join a Windows Server VM to an Entra Domain Services Managed Domain